Part 3: Enhancing ELK Stack Security - Creating an Elastic RTLO Binary Detection Rule
Having completed our observation on how the ELK Stack and Wazuh handle the detection of the proof-of-concept AI-synthesized malware, which I have named Predator, let's circle back and create an Elastic rule to detect Predator's Right-To-Left-Override (RTLO) file name, which it previously missed and therefore, no alerts were triggered. RTLO is a critical technique used by malware to disguise malicious files, making it an important focus for our detection efforts. In this article, we'll walk through the process of creating and implementing an Elastic rule specifically tailored to catch this evasion technique using the ELK Stack SIEM. By the end, you'll have a practical understanding of how to enhance your malware detection capabilities against this specific threat.
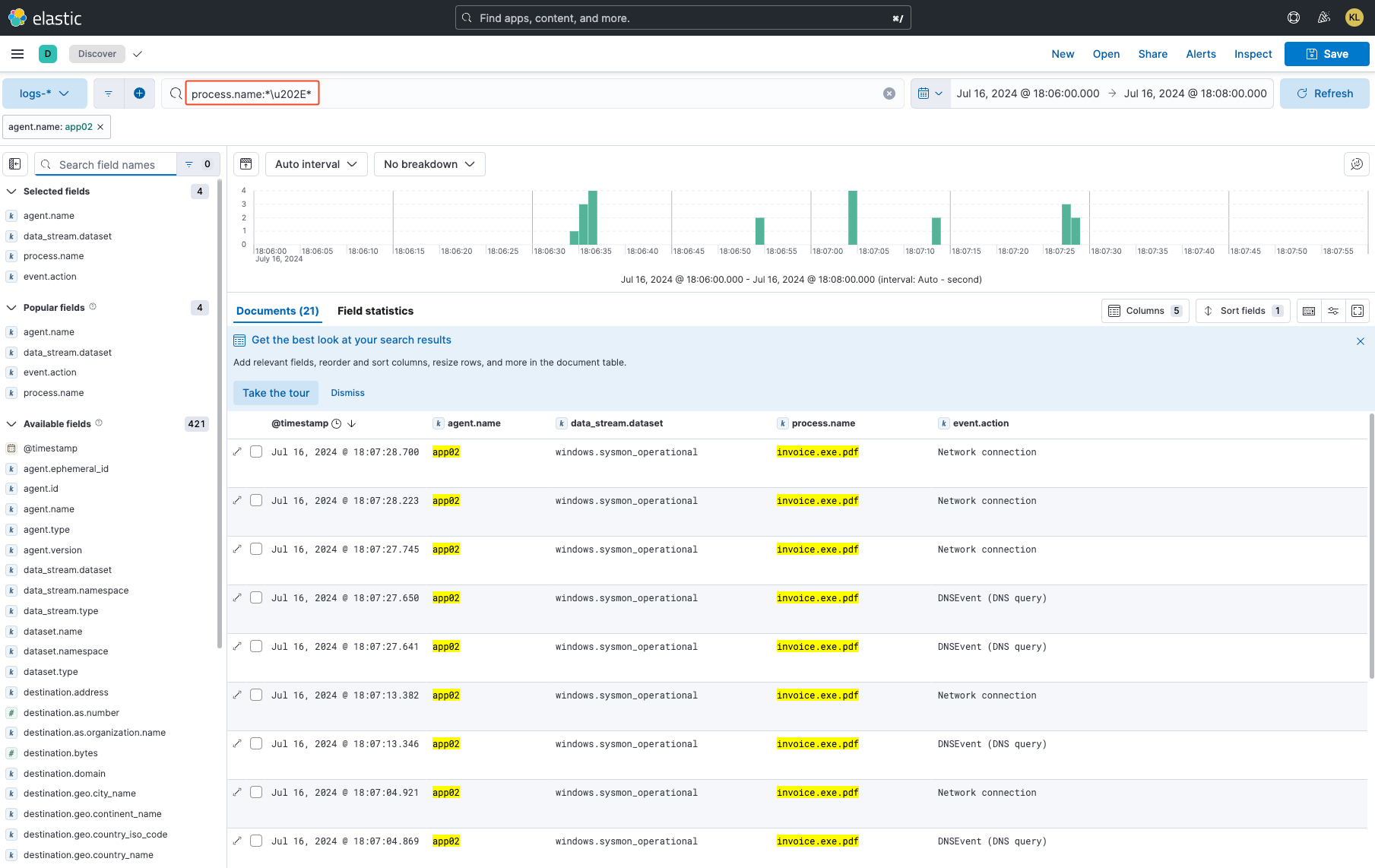
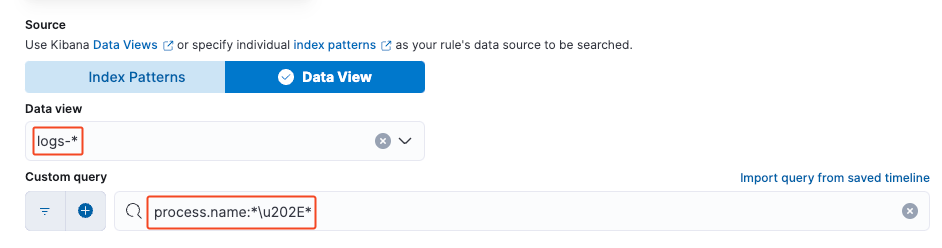
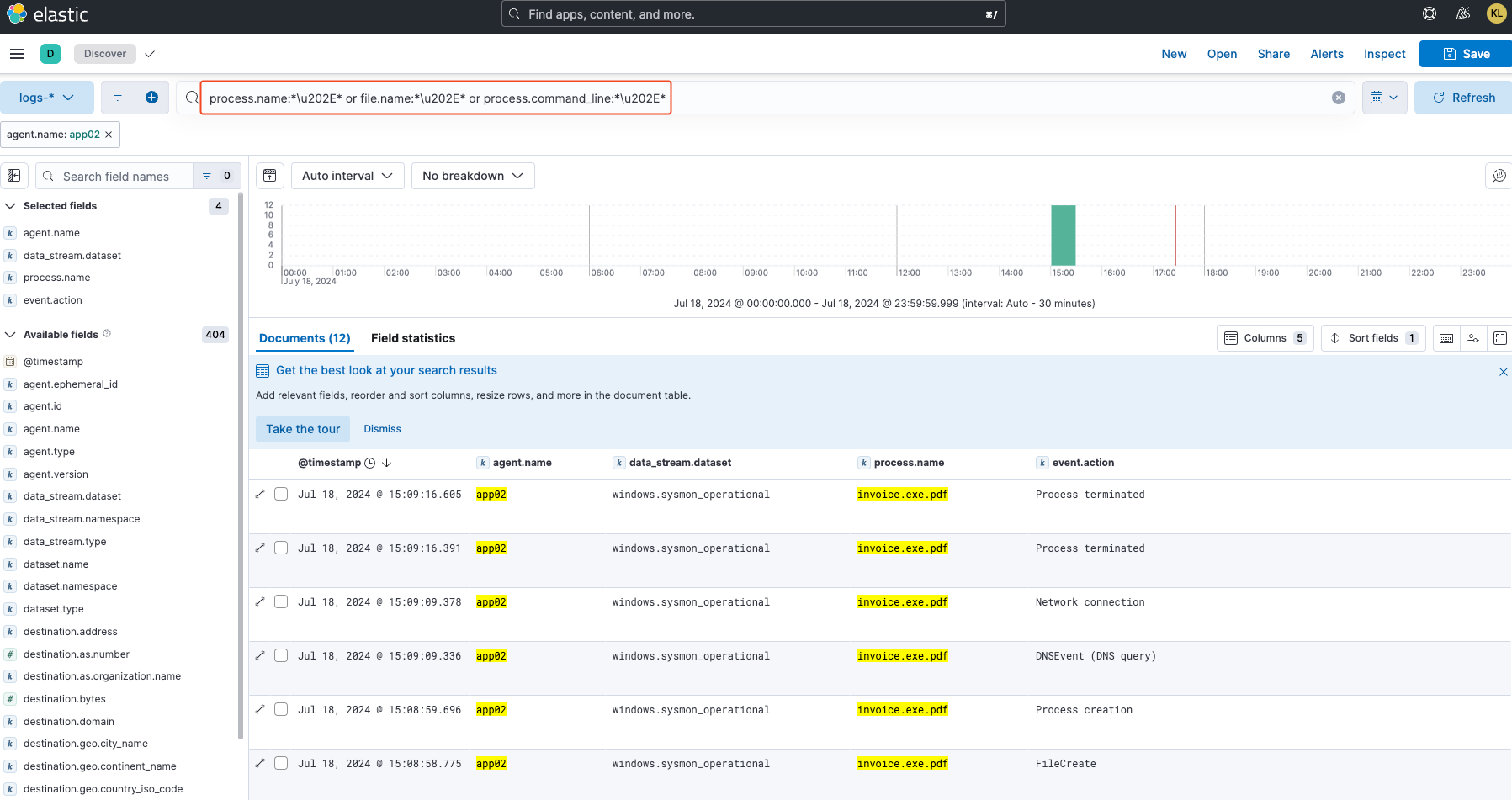
Knowing that Predator's file name uses RTLO, and with the help of online resources, I built the following simple KQL query filter: process.name:*\u202E*
As evident in the preceding image, the query successfully detected the malicious process invoice.exe.pdf. Now that we have confirmed its effectiveness, let's proceed to build the detection rule.
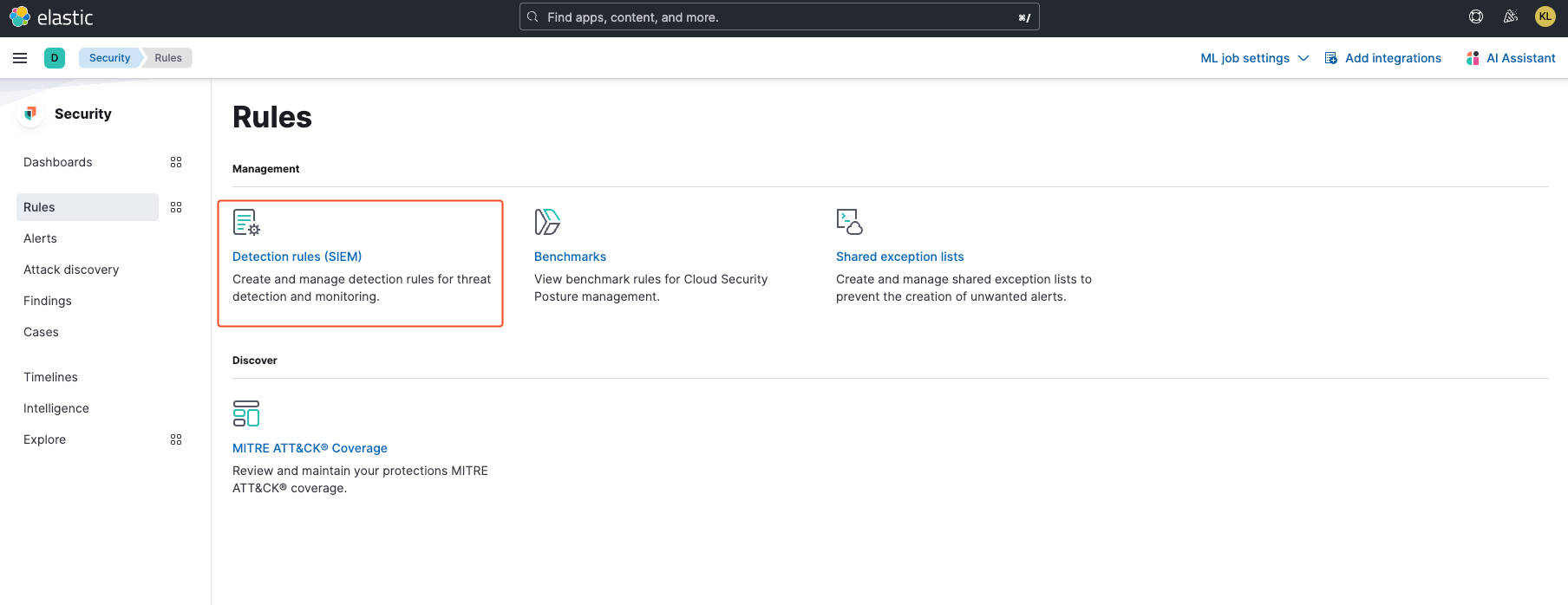
On the left side panel, under Security, click on Rules, then select Detection rules (SIEM).
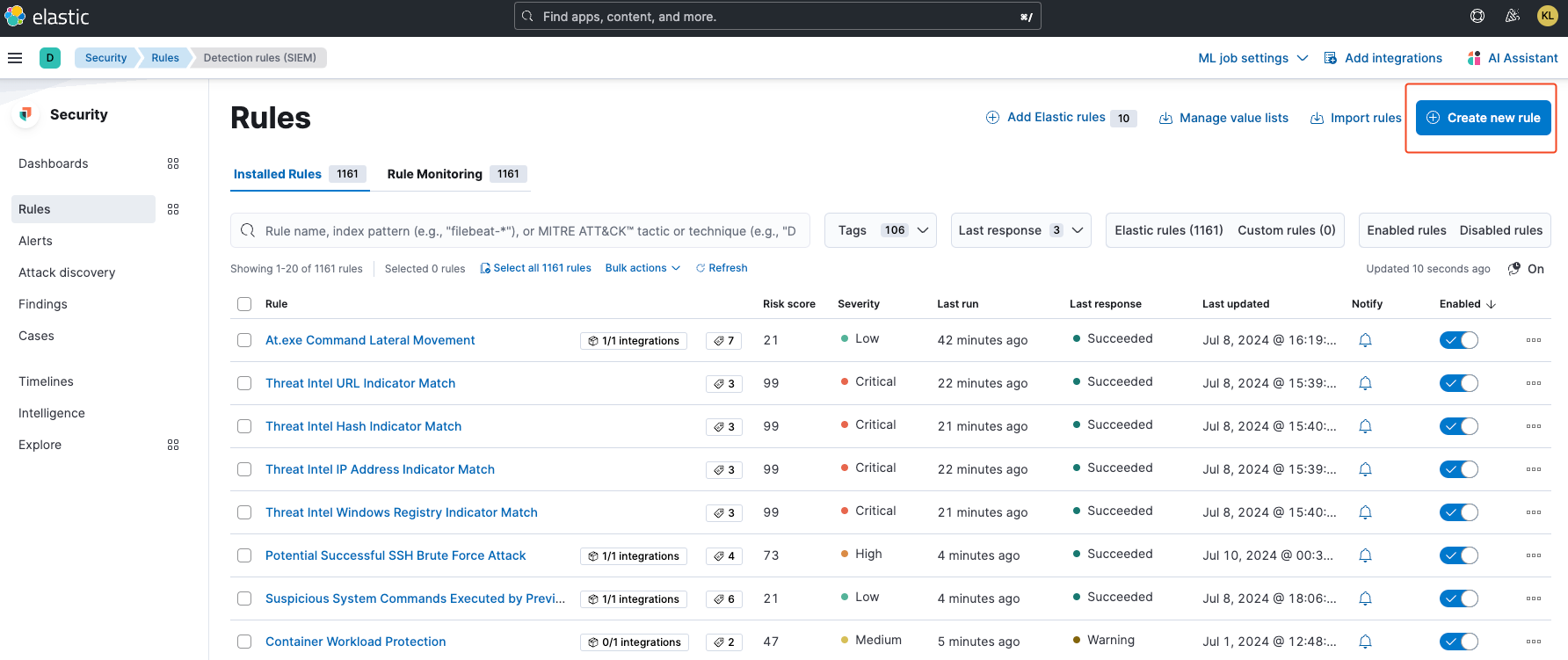
From the top right, click on the blue Create new rule button.
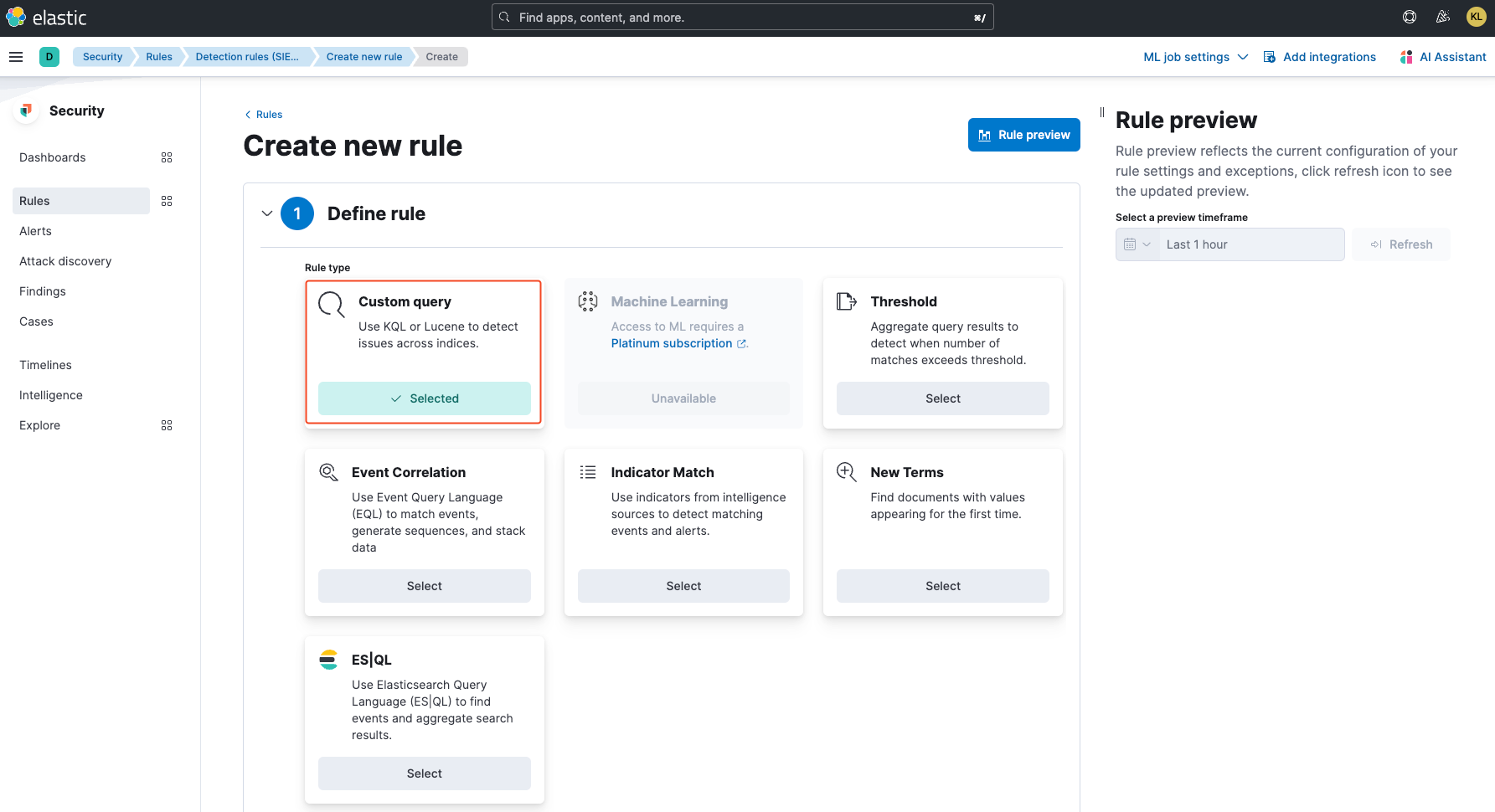
Next, in the Define rule section, select Custom query.
In the Custom query search bar, add the query process.name:*\u202E*
Next, in the About rule section:
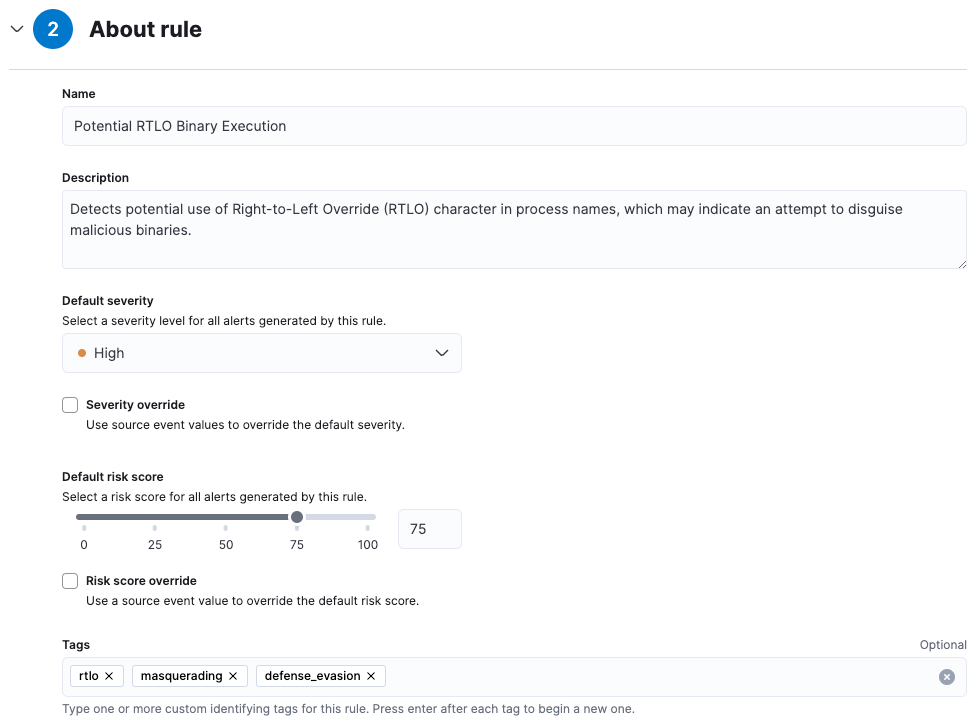
Add a name for the detection rule
Provide a description
Set the Default severity to High
Set the Default risk score to 75
Add the following tags:
rtlo,masquerading, anddefense_evasion"
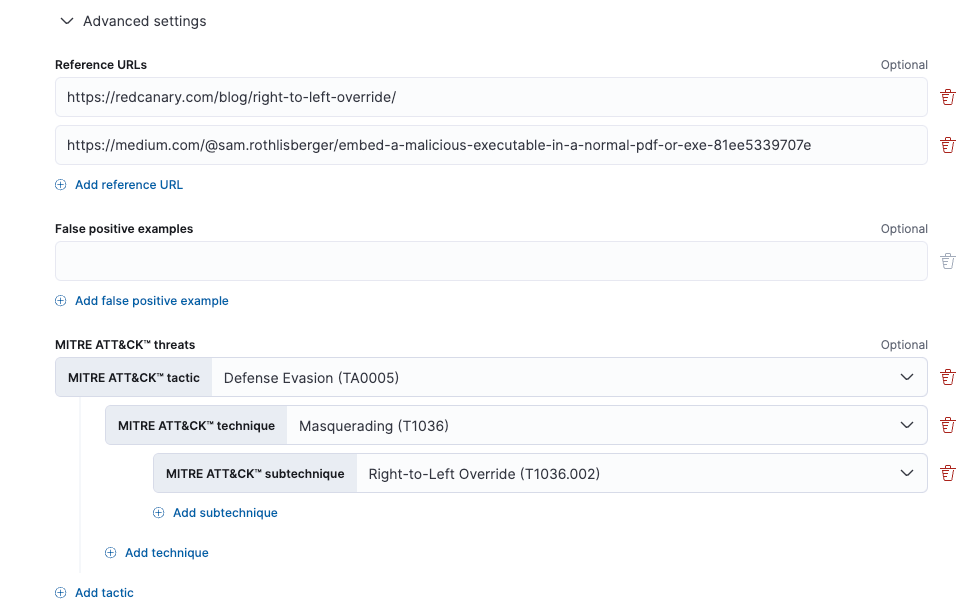
If desired, expand the Advanced settings section to add the following optional details:
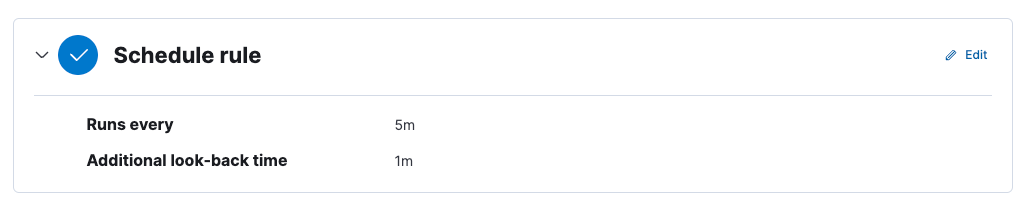
For the Schedule rule section, I retained the default settings.
To finish, click on the Create & enable rule button to activate the rule.
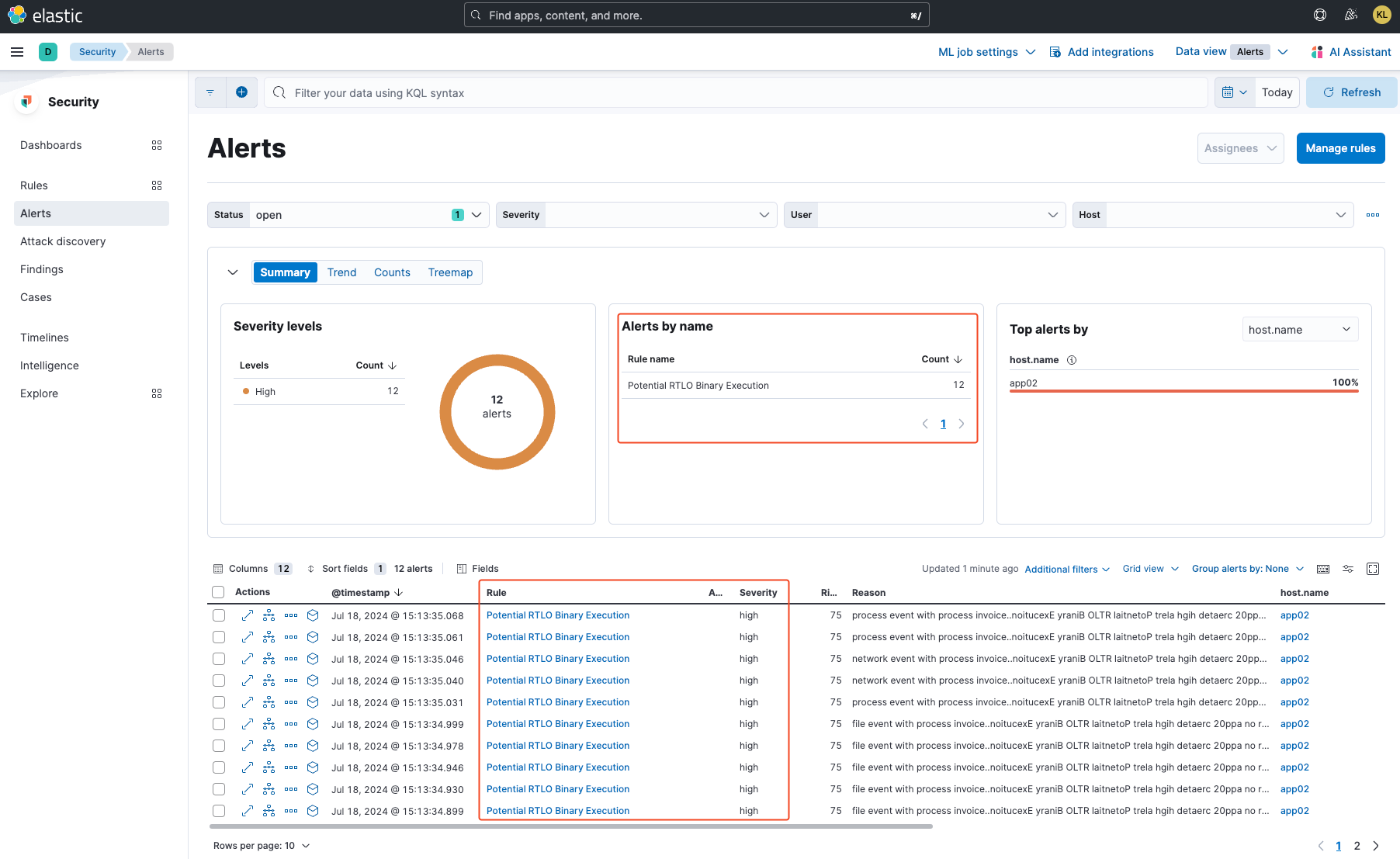
Now, let's verify whether this detection rule works. I proceeded to execute Predator, the invoice.exe.pdf file, and I can confirm that it worked. See the following alerts by going to Alerts on the left side panel under Security:
And there you have it. This is a simple detection rule created for the purpose of this article. However, you could enhance it for better detection capabilities. See the following image:
As we've explored, creating an effective Elastic rule to detect RTLO file names is a crucial step in enhancing your malware detection capabilities. By implementing this simple yet powerful technique, you're better equipped to identify and mitigate potential threats like Predator. However, our journey doesn't end here.
While the ELK Stack and Wazuh SIEMs can now detect Predator's activity through its RTLO method, we must consider scenarios where this technique isn't used. For instance, when the file name is left as is (e.g., acrobat.exe), we observed in part 2 that Wazuh didn't trigger high-level alerts except for the "Executable file dropped in folder commonly used by malware" alert. This alert is prone to false positives due to legitimate Microsoft System32 binaries also triggering it. As a result, analysts might ignore alerts that are true because they become accustomed to frequent false positives, potentially missing actual threats.
As a reminder from part 1 of this series, Predator itself is a benign executable with its configuration settings and malicious payload request prompt for the AI encrypted, making it even more challenging to detect without relying on the RTLO technique.
In the final installment of this series, we'll delve deeper into refining our detection strategies to stay ahead of evolving threats. I'll share my thoughts and recommendations on how to detect Predator and similar types of malware more effectively. We'll explore advanced detection techniques, the importance of fine-tuning SIEM rules to minimize false positives, and leveraging threat intelligence to enhance detection capabilities.
Remember, cybersecurity is an ongoing process – stay vigilant, keep learning, and continue refining your detection strategies. Thank you for following along in this series, and stay tuned for the final part where we'll take our malware detection capabilities to the next level.