Part 4: Advanced Detection Strategies for AI-Synthesized Malware
As the cybersecurity landscape evolves, AI-synthesized malware like Predator presents unique challenges that require innovative detection strategies. In this final installment of my series, we'll explore cutting-edge techniques for detecting such threats and leveraging AI-powered solutions to enhance cybersecurity defenses.
Monitoring Command and Control (C2) Traffic
For AI-synthesized malware like Predator that relies on C2 communication:
Network Traffic Analysis: Implement robust monitoring for unusual outbound connections, especially to known AI APIs or suspicious domains.
Discord Monitoring (Predator):
If Discord is allowed in your organization, implement strict monitoring and access controls, using Data Loss Prevention (DLP) tools to inspect traffic for potential data exfiltration.
If Discord is not permitted, configure your security tools to flag any processes attempting to communicate with Discord's servers as suspicious. This can help identify potential malware or policy violations.
Identifying Suspicious API Communications
To detect binaries communicating with known AI APIs:
Whitelist Management: Maintain a whitelist of authorized binaries allowed to access AI APIs.
SIEM Monitoring: Implement SIEM rules to flag any binary not on the whitelist that attempts to communicate with known AI APIs.
Suspicious Activity Investigation: Flag and investigate any unauthorized API communications for potential malicious activity.
Leveraging MITRE ATT&CK Framework
The MITRE ATT&CK framework can enhance detection strategies for AI-synthesized malware by providing a comprehensive knowledge base of adversary tactics and techniques:
Threat Modeling: Use the framework to model threats specific to AI-generated malware, identifying relevant tactics and techniques.
Technique Mapping: Map detection strategies to specific MITRE ATT&CK techniques, such as T1588.007, which covers the use of generative AI tools by adversaries.
Gap Analysis: Identify gaps in current detection capabilities by comparing them against the techniques listed in the MITRE ATT&CK framework. A tool I like to use for this is Tidal Cyber.
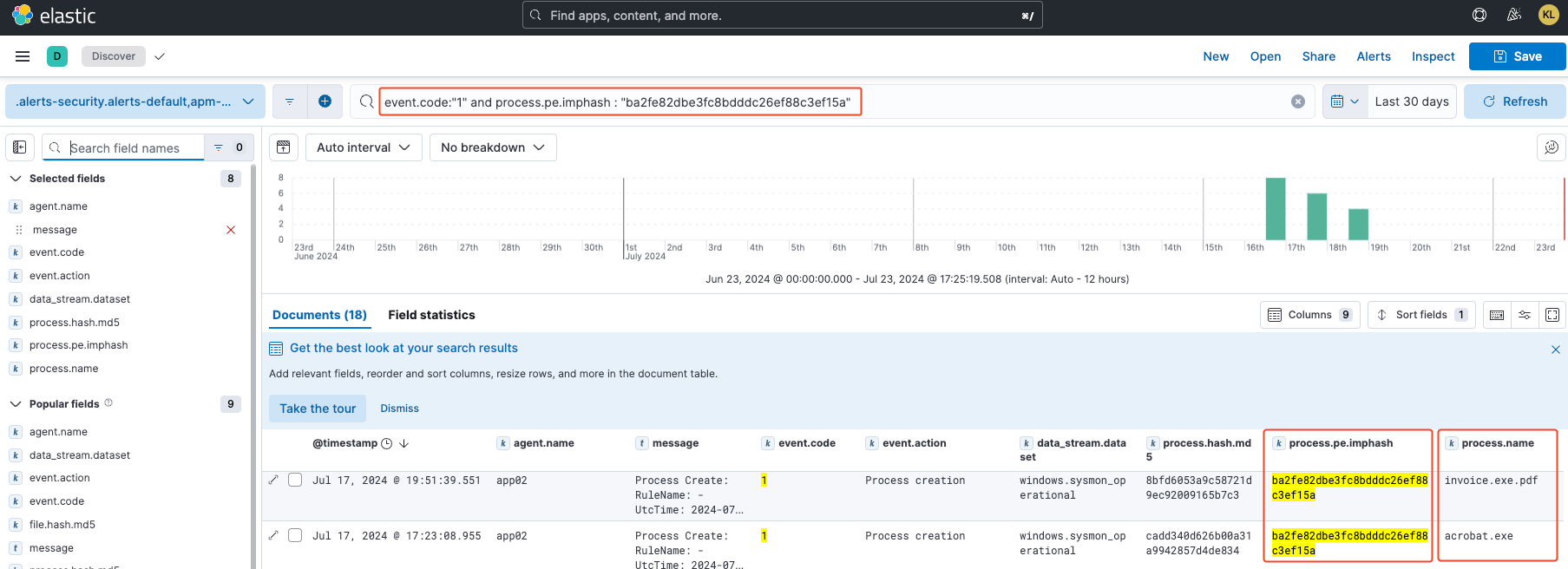
ELK Stack: KQL query filter for Predator malware using the IMPHASH. Here both instances are detected by this hash even though the MD5 hashes are different. Good technique for finding Predator variants with different MD5 hashes, however, Predator’s imports can be easily manipulated.
Fuzzy Hashing and IMPHASH
Fuzzy hashing, particularly using IMPHASH, is an effective technique for detecting Windows PE Predator variants:
IMPHASH for Detection: IMPHASH (Import Hash) is used to identify similarities in the import tables of PE files. This technique can detect Predator malware variants even if their MD5 hashes differ.
KQL Query Example: Use KQL (Kibana Query Language) to filter for Predator malware using the IMPHASH. For instance, a query like
event.code:"*" and process.pe.imphash : "ba2fe82de3fc8bdddc26ff88c3ef15a"can help identify Predator variants based on their import hash, as shown in the above image.Benefits and Limitations: This approach allows for the detection of different variants of the same malware family, improving the accuracy and efficiency of threat identification. However, it's important to note that import tables can be easily manipulated by adversaries to evade detection. This emphasizes the need for a multi-layered detection strategy that complements fuzzy hashing techniques with behavioral analysis.
Fine-Tuning SIEM Rules for AI-Synthesized Malware Detection
When developing detection strategies for AI-synthesized malware like Predator, it's crucial to balance efficiency with effectiveness. Here's an approach that leverages existing resources while allowing for customization:
Leverage Sigma Rules: Don't reinvent the wheel. The Sigma repository offers a wealth of detection rules that can be adapted for various SIEM platforms. Start by exploring and utilizing relevant Sigma rules as a foundation for your detection strategy. This approach saves valuable time and leverages the collective expertise of the security community.
Adapt and Customize: While Sigma rules provide an excellent starting point, customize them to fit your specific environment and the unique characteristics of AI-synthesized malware. This may involve adjusting thresholds, adding context-specific conditions, or combining multiple rules for more comprehensive detection.
Continuous Refinement: Regularly review and refine your adapted rules based on new threat intelligence and observed patterns of AI-synthesized malware. This iterative process helps reduce false positives and ensures that genuine threats are not overlooked.
Correlation Rule Optimization: Develop and fine-tune correlation rules that can link seemingly unrelated events that might be part of an AI-synthesized malware attack. This is crucial as these sophisticated threats often operate across multiple vectors.
Feedback Loop Implementation: Establish a feedback loop between your SOC team and rule developers. Insights from actual investigations can inform rule adjustments, improving detection accuracy over time.
Adaptive Rule Sets: Implement adaptive rule sets that can automatically adjust based on the evolving characteristics of AI-synthesized malware. This may involve using machine learning algorithms to update rules based on new threat intelligence.
By leveraging existing Sigma rules as a foundation and then customizing and refining them for your specific needs, you can significantly reduce development time while maintaining a robust detection capability for AI-synthesized malware. Remember, the goal is to build upon the collective knowledge of the security community while tailoring your defenses to your unique environment and the evolving threat landscape.
OpenCTI Platform provides comprehensive threat intelligence analysis and visualization, integrating seamlessly with cybersecurity frameworks to enhance situational awareness and response capabilities.
Leveraging Threat Intelligence
Effective use of threat intelligence is vital for staying ahead of evolving threats:
OpenCTI Integration: Utilize OpenCTI to enrich alerts with contextual threat intelligence.
Multiple Threat Feeds: Integrate diverse sources to ensure comprehensive coverage of emerging threats.
Community Collaboration: Participate in information-sharing platforms like MISP to stay updated on the latest threat intelligence.
Automated Updates: Implement systems to automatically update detection rules based on new intelligence.
CrowdStrike Falcon XDR leverages AI-native technology to seamlessly integrate data-centric security and IT automation, enhancing threat detection and response with advanced workflow automation as stated on their website.
AI-Powered Threat Detection
Leveraging AI for malware detection has become crucial in combating sophisticated threats:
Machine Learning Behavioral Analysis: Utilize machine learning algorithms to analyze file behavior and network traffic, identifying novel malware strains that traditional signature-based detection might miss.
Anomaly Detection: Implement AI-driven systems to analyze vast datasets in real-time, swiftly identifying anomalies and patterns that may indicate potential threats.
User and Entity Behavior Analytics (UEBA): Deploy AI to analyze user activity logs, identifying deviations from normal behavior patterns that could signal compromised accounts or insider threats.
AI-Enhanced Security Solutions
Consider implementing advanced AI-powered security solutions, including those offered by CrowdStrike Falcon, Palo Alto Networks Cortex XDR, and the ELK Stack with Wazuh:
CrowdStrike Falcon: Offers an AI-native cybersecurity platform that leverages machine learning for advanced threat detection and response:
Uses AI/ML to analyze file behavior and identify patterns indicative of malware
Employs behavioral analysis to detect and prevent sophisticated attacks
Integrates threat intelligence with AI to automate and accelerate investigations
Provides Charlotte AI, a generative AI security analyst, to accelerate investigation times
Palo Alto Networks Cortex XDR: Delivers an extended detection and response platform that uses AI and behavioral analytics:
Employs machine learning models to profile behavior and detect anomalies indicative of attacks
Utilizes AI-driven local analysis and behavior-based protection to spot stealthy endpoint threats
Offers automated correlation and grouping of alerts into incidents for faster investigation
Provides AI-powered vulnerability prioritization through the ExPRT.AI model
ELK Stack: While not inherently AI-powered, Elastic's machine learning capabilities can be integrated into the ELK Stack:
Offers unsupervised learning and preconfigured models for security issues
Provides actionable analytics to proactively surface threats and anomalies
Can be used in conjunction with Wazuh for enhanced threat detection and incident response
Wazuh: Though not directly incorporating AI, Wazuh can leverage AI capabilities through integration:
Integrates with Elasticsearch to utilize its machine learning features
Supports customizable rules and decoders that can incorporate AI-driven insights
Has explored integrations with AI tools like ChatGPT for enhanced security monitoring
By leveraging these AI-enhanced security solutions, organizations can significantly improve their ability to detect, prevent, and respond to sophisticated threats, including AI-synthesized malware like Predator. These platforms combine the power of machine learning, behavioral analytics, and human expertise to provide comprehensive protection across endpoints, networks, and cloud environments.
Post-Execution Analysis
While early detection is crucial, post-execution analysis provides valuable insights into AI-synthesized malware:
Behavioral Analysis: Monitor for unusual system activities post-execution. Examples include:
Lateral movements: Unexpected access attempts between systems or unusual network traversal patterns
Privilege escalation: Sudden changes in user permissions or unauthorized elevation of access rights
Abnormal data access: Large-scale data transfers or access to sensitive information from unusual locations or accounts
Unusual process execution: Execution of rarely used system utilities or scripts, especially those commonly used in attack scenarios
Changes to system configurations: Unexpected modifications to registry keys, startup items, or critical system files
Temporal Proximity Analysis: Correlate seemingly unrelated events based on their temporal proximity to identify potential malicious activities. For instance:
A series of failed login attempts followed closely by a successful login and immediate access to sensitive data
Installation of a new application followed by outbound network connections to unfamiliar IP addresses
User account creation or modification immediately preceding unusual data access or transfer activities
External System Analysis: Leverage multiple sources to gain insights into unusual system activities significant for post-execution behavioral analysis. Key activities to monitor include:
Unusual access patterns across multiple systems or cloud environments
Unauthorized data transfers to external locations or between internal systems
Modifications to critical systems or security configurations
Anomalous API calls or interactions with cloud services
Unexpected changes in network traffic patterns or volume
The main goal of post-execution analysis is to understand the malware's behavior, tactics, and impact. This analysis helps refine detection strategies, update security measures, and improve resilience against future AI-driven threats. By examining the malware's actions after execution, security teams can identify unique patterns or behaviors specific to AI-generated malware, enabling more effective prevention and faster response to similar threats in the future.
Conclusion
Detecting and mitigating AI-synthesized malware like Predator requires a multi-faceted approach combining traditional security practices with advanced AI-powered techniques. By leveraging machine learning for behavioral analysis, implementing robust threat intelligence, monitoring C2 traffic, and utilizing AI for both detection and analysis, organizations can significantly enhance their ability to detect and respond to these sophisticated threats.
Remember, the key to effective detection lies in continuous learning, adaptation, and collaboration within the cybersecurity community. As AI-synthesized malware continues to evolve, so must our detection and prevention strategies.
Thank you for following this series on SIEM and AI-synthesized malware detection. I hope you've found it informative and that you've gained valuable insights into the evolving landscape of cybersecurity threats and defenses. As the field continues to advance, staying informed and adaptable will be crucial in maintaining robust security postures. I encourage you to continue exploring and implementing these strategies to enhance your organization's cybersecurity capabilities.